An eCommerce site differs from other types of projects because of the customer contact information, payment details, supplier prices, inventory, and internal documents (invoices, orders, etc.). This data requires special care to protect it and ensure that it is stored securely. What makes a website secure and what is good for eCommerce site protection? We, at Brambling Tech, have created a guide for you to understand what is the best way to protect your website.
What is eCommerce or Electronic Commerce Security?
Basically, Electronic Commerce Security includes a compilation of guidelines and instructions that arrange safe and secure transactions and other security features for an eCommerce website. The rules and protocols of eCommerce provide safety for people who participate in the process of online sales. There are four main rules of how to secure a website that sells goods or services and as an online entrepreneur, you probably should know them.
The 4 Pillars of eCommerce Security
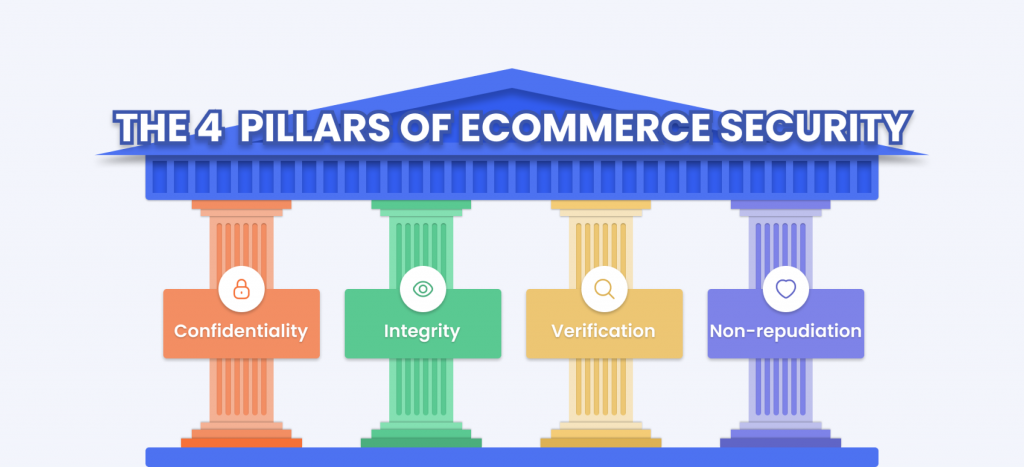
Confidentiality
Confidentiality or privacy is a major feature of a safe and secure eCommerce site. It includes eliminating any malicious activity that can result in a customer data leak. A user should be ensured that their personal information is shared only with the store where they want to make a purchase.
A data leak can happen if the site uses unauthorized third-party apps or services. Therefore for an online business, it is important to provide at least the bare minimum of privacy protection. Using antivirus software, firewalls, certificates, and other encryption tools will be a perfect solution for ensuring your customer’s and eCommerce website security.
Integrity
Speaking about the main rules of eCommerce security, there’s no way we couldn’t mention integrity. It means that the information a user provides remains unchanged. For an online business, it is a responsibility to keep and use the given data unaltered, and the user is responsible for providing accurate details of the information.
Verification
Another option of e-commerce security measures is authentication. This rule means that both the user and the store are real and they are who they are. To prove their identities, the store and the customer must provide proof for each other for an online business for both parties to feel safe. Verification of identification can be done by using the signing up process, etc.
Non-repudiation
From an information security perspective, non-repudiation usually applies to cases of a formal contract, communication, or data transfer. Its purpose is to ensure that the individual or legal entity bound by the terms of the contract, and eliminate or the parties involved in the particular exchange of information or transfer of documents, cannot deny the authenticity of their signatures on contract documents or that they were the senders of a particular message or data.
Why Can’t You Afford to Overlook eCommerce Security?
The awareness of online store owners about the possible consequences of hacking a site is at an extremely low level. And this is sad because the results of hacker attacks can lead to the worst options of the security risk of e-commerce. For example, blocking of an online store by search engines for spreading viruses, explicit content, or malware; restricting access to the site by the hosting provider for sending spam and phishing emails; hacker blackmails, etc.
Unfortunately, the virus market is developing faster than antivirus software. Malware and hackers are always one step ahead of antivirus programs and the white knights that protect your website. Don’t even doubt investing in a good system of website protection.

For e-commerce companies, the most sensitive are targeted attacks. The purpose of these attacks is to gain access to the personal data of customers, various types of fraud (with bonuses, promotions, personal accounts, electronic payments), web scraping, and DDoS attacks. According to StormWall’s research on the dynamics of DDoS attacks on online retail companies, in the period from February to September 2020, the number of such attacks quadrupled compared to the same period last year.
Main eCommerce Safety Risks & Issues
If you still think that your online store can get along without complex security options, you should consider what can happen and learn about the ways to protect your business website from hackers.

DOS/DDOS attacks
An online store involves a huge number of users and requests every day. The system administrator’s task is to correctly distribute traffic so that the server does not get covered and the site does not fall. After all, a day of downtime can cost the owner from several hundred to thousands of dollars. That’s why you have to protect your website from DDoS attacks.
A similar situation can be created on purpose, for example, during the sales or holiday season. The scheme is simple: an attacker creates conditions where the site server will not withstand the load.
A DOS attack involves a large number of requests from a single IP address. Most likely, your firewall will block such manipulations. In the case of DDOS, an abnormally large number of requests are sent from several IP addresses, which the firewall can recognize not as an attack, but as requests from users.
SQL Injection
Quite simply, SQL injection is an attack on a database to gain profit. Any site has contact forms where the user enters their information and this personal data (phone number, email, and name, card number, or document) can be stolen easily. The data entered by the user is sent to the server where the database is stored. A hacker only needs to find an unsecured contact form to inject a piece of code there that will change the logic for returning a request. Thus, it will intercept the data entered by your user.
But why would a hacker steal consumer’s data? For example, a list with contact details can be profitable to sell to your competitors. They, in turn, can make a newsletter with the terms of the promotion, for example. This way, your potential customers will become your competitor’s real customers.
Backdoor
Online stores usually want their customers to register for further purchases. The personal account usually stores a password, contact information, and order history. Sometimes, there’s also a request to upload a photo. But if it’s not a social media site, then why would you do that? The answer is simple: uploading a photo can “open a door” for hackers to provide malicious code. The logic of this code contains a command that searches for passwords to the database, server, admin panel. The file format changes from jpeg, png, any other picture-suitable format into PHP.
10 Solutions for eCommerce Security
Don’t hesitate to dig into the website security for eCommerce sites. Remember that even outdated versions of software can become a weak point and allow cybercriminals to gain access to information that is important to you.

Switch to HTTPS
For the security of data transfer, experts advise using the HTTPS protocol, since:
- any information entered using SSL is encrypted, therefore, in case of interception, the attacker receives a random set of characters;
- when sorting sites for issuance at the user’s request, search engines react to the presence of a domain name, SSL certificate, and quality content;
- if the connection is not secure, then the Chrome and Firefox browsers will issue a special warning to the user about the absence of an SSL certificate.
Google developers specifically made having an SSL certificate one of the security measures for e-commerce sites an advantage of search engine ranking to encourage users to protect their resources and make the Internet safer.
Safe gateway for payments
A payment gateway is a service provider for processing payment transactions for goods and services. Connecting an online store to a payment gateway can solve all issues with payment on the site since a huge number of different methods will become available for payment, convenient for the end client, and the entrepreneur. In addition, payment gateways are easier to integrate into any website or online store, thanks to the support of a huge number of CMS or the ability to connect to the gateway using the API. You need to check the best payment gateways for e-commerce and choose the one that provides secure payment options for your customers.
More than 80% of consumers feel safe seeing the logos of the trusted payment services used on the site. You will have to pay a commission for transactions carried out on behalf of your company. Therefore, pay attention to the cost of services of the selected payment gateway. These fees may include transaction fees, statements, refund fees, account management fees, and fees for using a particular payment method.
Get antivirus software
Web sites, as well as electronic devices, need anti-malware programs for avoiding viruses and protecting your website from an attacker. Investing in anti-malware or antivirus software helps to keep you updated about possible attacks and actions that lead to stealing data.
Use firewalls
As for the functionality of the firewall, it can control and protect the website at many stages. It controls application access to ports, actually allowing or denying access to the network. As a rule, firewalls are different and depending on the type of installed firewall, it can either increase the level of protection or lower it. There are three main types of firewalls: filter, SPI technology, and application firewall.
Get SSL certificates
Having an SSL certificate is proof of the security of the site and is the easiest way to protect your website. It is indicated by a green lock in the browser’s address bar, in front of the site address. If you click on it, you will see a message stating that the connection is secure. Also, the letters HTTPS in the website address indicate security. When the connection to the site is not secure, the browser will show users a message that the site has an unsecured connection and that they may become a victim of scammers. This can significantly reduce conversion rates because few people want to leave data on a site from which they can be stolen.
Reasons why you need an SSL certificate:
- Each company that requests contact information to register on the site becomes the operator of users’ personal data and undertakes to ensure their protection;
- The use of a secure connection protocol is one of the ranking factors for Google, as they stated in their blog back in 2014;
- The presence of a green padlock with the inscription “Secure connection” is a factor that positively affects the trust of visitors to the site.
Apply eCommerce security plugins
Being into the eCommerce business requires the best security plugins. This helps you to stay protected on many stages, including the protection of connection, protection of the site data, and protection of user’s personal information on their account.
Backup your data
Creating a safe copy of the data and storing it in a secure place is a must. This will help you to return the information you might have lost after the attack quickly and probably painless. If you have a backup copy of the online store files, databases, messages, customer base, product database, content, and transactions history, you will restore the information at any time (which usually comes at the most inopportune time) in the shortest terms.
Stay updated
An online store, as the main trading tool, should work stably and smoothly. To ensure these conditions, you have to provide proper attention to the security of the resource, which means organise a site security audit. A routine procedure (for example, once a quarter) for doing an information system security audit allows assessing the maturity of the information security management system and identifying vulnerabilities for their prompt elimination. It is necessary to maintain the relevance of the used components of the information system both CMS and its components. The importance of updates and their timely installation is obvious to maintain an appropriate level of information security.
Choose a reliable eCommerce platform
Hosting is a key component of a secure online store. The speed of loading the site pages, the reliability of the work, and the safety of the entire project directly depend on your choice of platform. In simple words, hosting is site storage that contains information about resources, files, databases, backups, etc. After a site is placed on hosting, it becomes available on the Internet.
Take care of your staff & clients
It is necessary to make sure that the personnel and your customers are aware of the possible fraud. Give instructions to the admins so they know the steps to protect your website. And also create educational sections for clients to help them avoid fraud.
Summing It Up
Your customers need to be aware that you are following all possible security measures for an e-commerce website to be safe. To keep your online store updated and safe for your clients, test it regularly, fix issues if they are found, and make sure that all vulnerabilities are under your control and you can protect your website from cyber attacks.